The Leaked Key: Protecting Your Account from Unauthorized Promo Code Use
- Category: Pics |
- Yesterday, 00:02 |
- Views: 126 |

Promo codes are designed to be incentives, but when they are personalized and unique—intended for a single user or a small, exclusive group—they represent a form of digital currency tied directly to a user's account or financial benefit.
The security of these unique codes is paramount. If a personalized code is leaked or guessed by a fraudster, it poses two immediate risks: financial loss for the operator through unauthorized redemption and, more importantly for the user, a potential account compromise if the code is part of a phishing attempt. Protecting these digital assets requires a shared responsibility between the platform and the user, particularly in high-stakes environments like NV online casino, where financial transactions are common.
For the user, safeguarding the account is the final defense against unauthorized use, especially when dealing with one-time or high-value personalized offers.
The Operator's Defense: Security by Design
A reputable online platform utilizes several technical safeguards to prevent unauthorized code use and account breach:
1. Unique code generation. Instead of simple, guessable generic codes (like "SAVE10"), operators generate complex, randomized, alphanumeric codes tied to a specific Customer ID or affiliate tracker. This prevents dictionary attacks and makes guessing virtually impossible.
2. Usage limits and eligibility checks. Codes are programmed with strict parameters: a single-use limit, an expiration date, and eligibility criteria (e.g., "only valid for accounts registered in Nevada"). This ensures that even if a code is leaked, its usability is severely restricted to the intended recipient.
3. Real-time monitoring and flagging. Advanced anti-fraud systems continuously monitor redemption attempts. They automatically flag and block usage spikes, redemptions from unusual geographic locations (outside the intended region), or multiple redemptions from the same IP/device, which indicate a leak or automated abuse.
These measures are the first line of defense, mitigating large-scale public exploitation of a private code.
The User's Defense: Account Hardening
The most effective protection against unauthorized code use and phishing attempts rests with the individual user. Fraudsters often use fake codes or leaked codes in social engineering attacks to try and gain access to account credentials. Essential steps for account security:
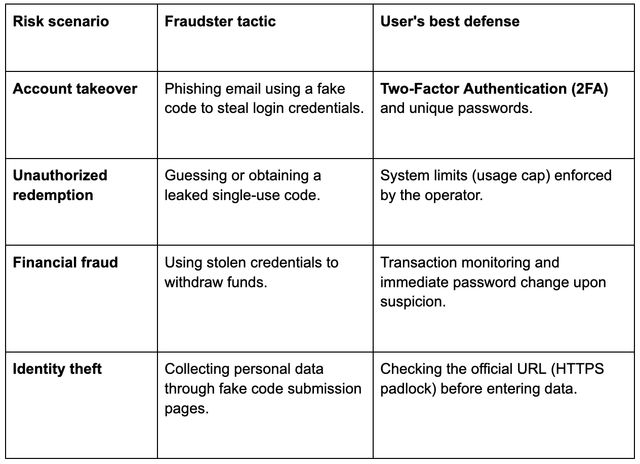
The responsibility for core account security ultimately lies with the user, and the most critical defense against the primary threat (Account Takeover via phishing) is the implementation of Two-Factor Authentication (2FA). This measure creates a fundamental barrier that prevents a fraudster from utilizing stolen credentials, thereby protecting both the account balance and the integrity of promotional code usage.
Leaks and Responsibility: Why Code Sharing is Risky
When a unique, private promo code is intentionally shared by the recipient on a public forum or social media, the user is directly responsible for that action.
• Code Invalidation: The operator's fraud detection system will quickly flag the code for unauthorized public distribution and immediately invalidate it. This means the original, legitimate user loses the benefit.
• Risk to Account: Excessive, abusive sharing of private codes can be interpreted as a breach of the operator's terms and conditions, potentially leading to account suspension or closure.
For the user, the safest practice is to treat a personalized promo code like any other sensitive credential—it is an exclusive benefit to be used only by the intended recipient via secure channels.
Proactive Security: Your Digital Vault
The security of a promo code is inherently tied to the security of the user's account. While operators must deploy strong anti-fraud technologies, the user is the final security layer. By adopting robust practices like 2FA and constant vigilance against phishing, you ensure that any unique, valuable offer intended for you remains yours and that your digital assets are protected from unauthorized access. Have you activated Two-Factor Authentication on your gaming account today?

